How an endpoint security company’s global outage highlighted the need to focus on supply chain risks
An American cybersecurity technology company’s global outage made headlines after it affected supply chains considerably. Millions of flights across the globe were cancelled. Emergency services, credit card payments, medical and even banking services faced considerable disruptions. Employees in organisations were affected by a blue screen that flashed on their monitors and caused the systems to restart continuously.
Was the security company identified as a key third party or a fourth party across organisations?
Today, most organisations rely on third parties for services like cloud storage, IT support, outsourcing of admin functions and many more processes. While Microsoft might be listed as a third party for such organisations, the important question to ask is whether the endpoint security company was listed as a sub-contractor of Microsoft. The answer lies in asking organisations if they were mapping their fourth parties. Furthermore, we believe that organisations that map fourth parties may have also missed listing the cybersecurity firm as a fourth party, since the typical definition of the same is ‘material subcontractors who deliver services or components to the third party’, while the cybersecurity firm was a ‘material contractor providing critical software to a third party’.
Why do we need to identify and monitor fourth parties?
Over the last few months, we have had many conversations with clients focusing on the importance of identifying and continuously monitoring high-risk fourth parties and not relying on traditional checklist-based, point-of-time assessments limited to third parties. As the Microsoft incident highlighted, many third parties outsource work or rely on services by their third parties, and might end up sharing critical or sensitive information about our organisation. This exposes our organisations to data privacy or cyberattack risks due to the security posture of all third parties involved in delivering work or services to us.
The need for managing supply chain risks
As organisations rely increasingly on the complex network of third- and fourth-party vendors, the potential for cybersecurity vulnerabilities and operational disruptions increases. Compliance with regulations such as the Digital Operational Resilience Act (DORA) emphasises the need for supply chain transparency and oversight, including fourth-party relationships. Thus, compliance becomes critical for maintaining operational integrity and trust. Stringent data protection measures are becoming more and more important as the sharing of proprietary information (PII) with third parties exposes organisations to the risk of data theft. The rapid adoption of artificial intelligence, including GenAI, means additional data safeguarding measures must be implemented to ensure AI tools and solutions are secure and compliant. Also, the increased focus on the procurement of software highlights the importance of assessing and mitigating risks associated with software supply chains. Therefore, ensuring all software components are secure and reliable is critical to safeguarding the entire supply chain.
How to manage and mitigate third- and fourth-party risks across your supply chains
Given below are 5 key steps organisations can take to identify, assess, monitor and mitigate supply chain risks:
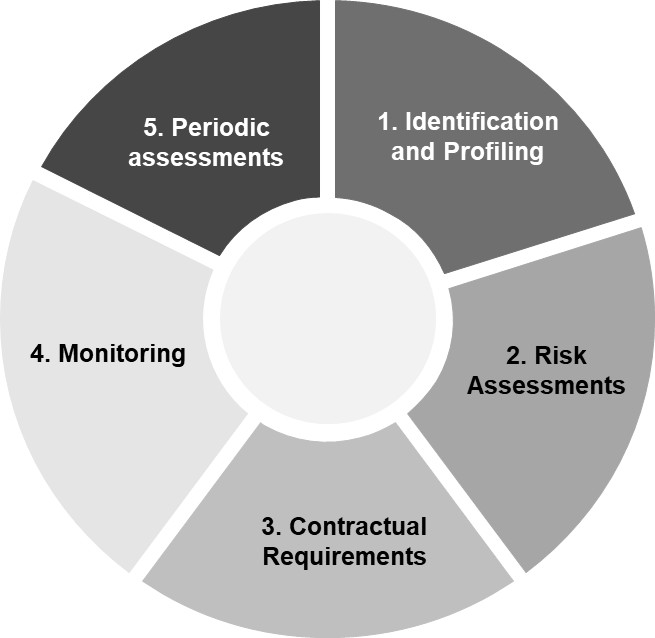
- Identification and profiling
Identify all third and fourth parties used across your organisation to profile them based on their inherent risk exposure. Also ensure mapping of software providers used across your supply chain. - Risk assessments
Asses third parties across traditional and emerging risks including regulatory, reputational, financial, operational, health and safety, environmental, social and governance (ESG), information security, data privacy and business continuity through screening, external security ratings and questionnaire-based assessments. - Contractual requirements
Ensuring the right clauses (like IT security requirements, flow-down clauses, data restrictions, business continuity plan (BCP) testing, right to audit, anti-bribery compliance etc.) has been incorporated as per the risk posed by the third party in contracts. - Monitoring
Keep track of the daily feeds from security rating agencies and compliance databases (including dark web and fourth party for critical third parties), and review and determine the severity of the red flags. Threat monitoring is also vital as it assesses the credibility, impact and severity of the flagged incidences at a threat actor level. - Periodic assessments
Perform periodic risk assessments based on the criticality of third and fourth parties – which can be trigger-based or at a defined frequency.
What are the challenges organisations face while managing supply chain risks?
- Inadequate third-party risk management framework
Many organisations lack a comprehensive framework to manage risks associated with third and fourth parties. This gap can lead to vulnerabilities and inefficiencies in risk mitigation efforts. - Lack of inventory of third and fourth parties
Without a clear inventory of third and fourth parties and their risk exposure, organisations struggle to understand and manage their risk landscape effectively. - Limited visibility over software supply chain
Organisations often have limited visibility into their software supply chain, making it difficult to identify and address potential vulnerabilities and risks. - Lack of comprehensive assessments
Comprehensive assessments of third parties on critical areas such as cybersecurity, data privacy and business continuity are often lacking. These assessments are essential for identifying and mitigating risks. - No monitoring of supply chain threats
Continuous monitoring of supply chain threats, vigilance over potential vulnerabilities and oversight of fourth-party risks are important for maintaining a secure and resilient supply chain.
Some lessons learnt from the global outage incident have been outlined below:
Identify all third parties and critical fourth parties across the supply chain
In today’s rapidly evolving world, knowing and managing your third-party risks is not enough, as made evident from the global IT blackout incident. Tracking the entire supply chain and identifying fourth parties/material subcontractors will help in developing a resilient third-party risk management (TPRM) process.
Identify software-related fourth-party risks
While TPRM traditionally involved identifying and managing risks related to direct material and service providers, identifying and managing all the software/technology risks associated with third parties is also equally important. Even one vulnerable technology/service can easily compromise your vital applications and platforms and bring business to a standstill.
Manage fourth party risks across your supply chain
As supply chains become more complex, identifying the key fourth parties/subcontractors being used to deliver work and services indirectly to your organisation becomes critical.
To summarise, as supply chains become more complex, it is essential to design and implement a risk-based monitoring process to assess, manage and mitigate third- and fourth-party risks across the supply chain.
Author
Anu Purkayastha
Partner – Risk Consulting, PwC India, PwC India













